Introduction
The use of Amazon Web Services(AWS) has become increasingly popular as organisations are moving their IT workloads to the cloud and cloud service providers(CSPs). According to reports by analyst firm Gartner, the cloud service provider infrastructure-as-a-service(IaaS) market is predicted to grow by 35.9% in 2018, reaching $40.8 billion by the end of the year. The adoption of IaaS shows no signs of slowing down and the total market is expected to reach $83.5 billion by 2021. (Gartner report https://www.gartner.com/newsroom/id/3871416).
Amazon Web Services has a 41.5% market share of all workloads deployed to the cloud, outnumbering Microsoft Azure, Google Cloud Engine, IBM Softlayer and Rackspace combined as can be seen in the chart below. This article will focus on Amazon AWS and how to integrate and configure Google G Suite user authentication to AWS.

Moving IT workloads to the cloud in a secure way depends on robust, documented and monitored Identity and Access Management procedures. Using SSO for provisioning and managing access to the CSPs is a good best practice that should be considered by organisations using cloud services.
This article shows how Amazon Web Services(AWS) can be configured for SSO with Google G Suite using SAML 2.0.
Configuring SSO for AWS using Google G Suite
In order to configure SAML authentication to Google G Suite for AWS the following steps needs to be done:
- Create a SAML App in Google Admin console
- Create an IDP(Identity Provider) and Role in AWS IAM
- Configure AWS IAM role attributes for Google G Suite users.
- Enable SAML App in Google G Suite
- Verify that SSO login to AWS using Google SAML App works
- Done
Step 1: Create a SAML App in Google Admin console
First we need to create a SAML app in the Google Admin console. Go to the Admin Console and then to Apps and SAML Apps. There create a new SAML app and choose Amazon Web Services from the list. Go forward and download the IDP Metadata file and then continue until the user attribute mapping page:







Here you need to map the Basic information and IAM_role attributes and additionally add the following attribute:
- https://aws.amazon.com/SAML/Attributes/SessionDuration
- AWS SAML
- SessionDuration
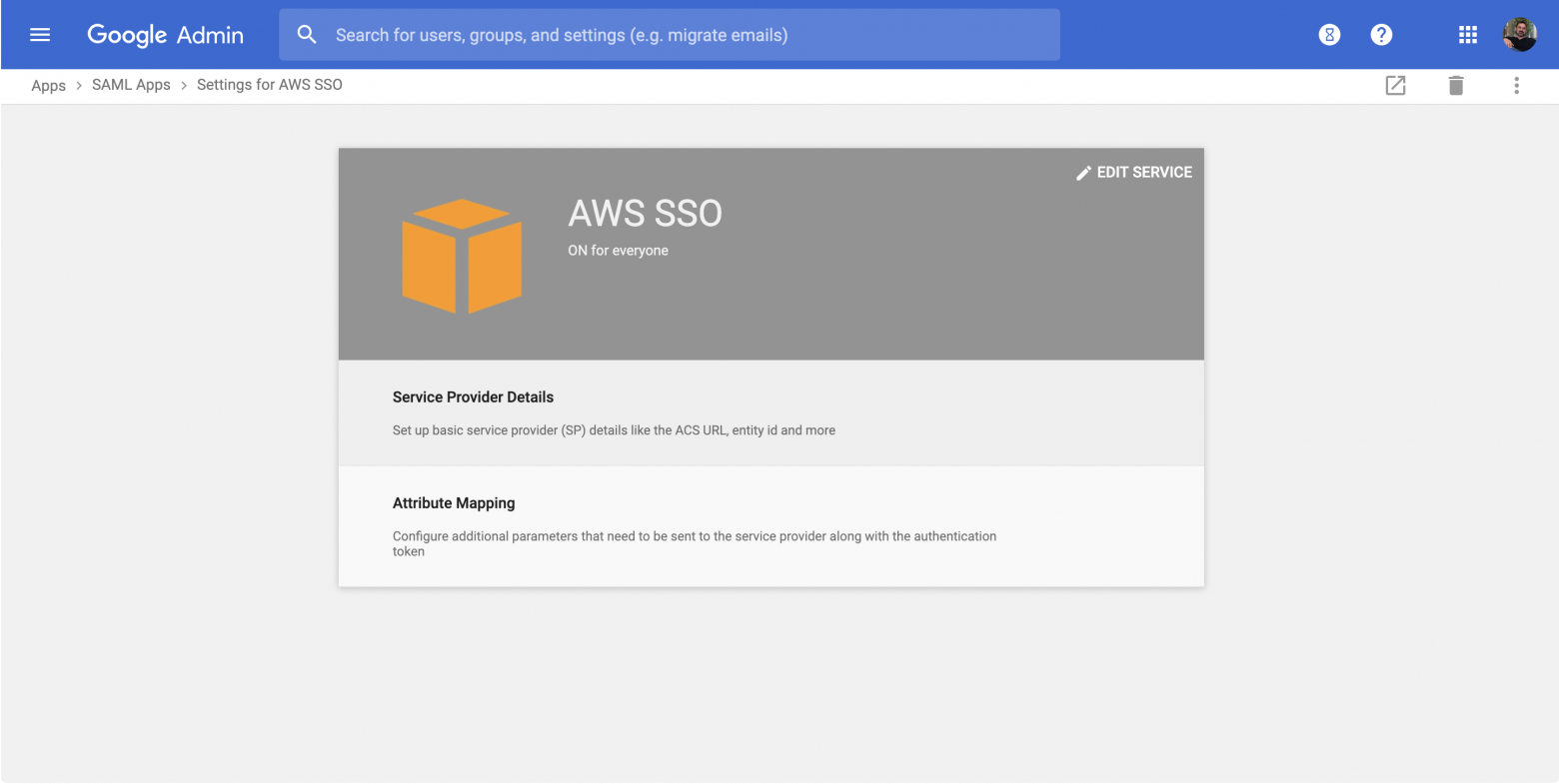
When you are done you will have a SAML App called AWS SSO:




Step 2: Create an IDP(Identity Provider) and Role in AWS IAM
The second step we need to do is to create a SAML Identity Provider in the AWS Management Console IAM resource section. Creating an IDP resource is very straightforward, you just need to choose a unique name for the resource. In my example screenshots below I have named my IDP resource google-gsuite-IDP in order to have a meaningful name for the resource and so that it is easy to distinguish from other IDP resources I might add in the future.


Here you need to upload the Metadata file downloaded previously when creating the Google SAML app


Click on the IDP and copy the the Amazon Resource Name(ARN) for the created IDP resource. The ARN has the following format:
arn:aws:iam::account-id:saml-provider/idp-name
The ARN will be used in the following steps.
Next we need to create a IAM Role that the SAML authenticated users will get mapped to. In this example I am creating a role with a ViewOnlyAccess policy that will be used for granting read-only access for Google SAML authenticated users.




Click on the IDP and copy the the Amazon Resource Name(ARN) for the created Role resource. The ARN has the following format:
arn:aws:iam::account-id:role/role-name
The ARN will be used in the following step
Now we are done with creating the Google SAML app and AWS IDP. Next we will configure the Google users and map them to the appropriate role.
Step 3: Configure AWS IAM role attributes for Google G Suite users.
Next we need to configure Google users with additional attributes used in the previous steps. . This has to be done for each user that needs to have access to the AWS SAML login.
Here we use the AWS ARNs for the role and IDP that we noted before and add them to the AWS SAML attributes for the user:
arn:aws:iam::account-id:role/role-name, arn:aws:iam::account-id:saml-provider/provider-name

Step 4: Enable the Goole SAML app in Google Admin console
Make sure that the Google SAML app is enabled for your users. This can be seen in the SAML Apps directory in the Status column. The app will be OFF for everyone and has to be enabled. Click on the three-vertical-dots icon to the right of the application and choose “ON for everyone”. Now the application is enabled and can be used by users with the appropriate attributes mapped!

Step 5: Verify that the SSO login to AWS using Google SAML App works
Next we will test that the Google SAML app works. Make sure you are logged in to Google G Suite and then click on the apps icon on the top right. Scroll down the applications list and clic the AWS SSO application. This should take you to AWS Console with read-only access as configured in the steps above.

Step 6: Done
We are now done with configuring Google SAML authentication for AWS console.
Worth noting:
- You need to configure the SAML attributes for all Google users that need access to AWS
I hope this has been informative and helped you configuring Google G Suite SAML with AWS.
If you need any help with configuring Google G Suite or AWS? don’t hesitate to contact us at Deductive Labs!
References
- https://www.skyhighnetworks.com/cloud-security-blog/microsoft-azure-closes-iaas-adoption-gap-with-amazon-aws/
- https://www.parkmycloud.com/blog/aws-vs-azure-vs-google-cloud-market-share/
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_saml_3rd-party.html
- https://support.google.com/a/answer/6194963